Cicada 3301
On January 2, 2012, a puzzle emerged on an image board called 4chan. What first appeared as a simple game of puzzles to be solved quickly morphed into a global enigma. The entity, or perhaps individual behind Cicada 3301, has remained shrouded in anonymity, yet their penchant for insanely complex challenges aimed at code-breakers across the digital domain has become a hallmark of their existence.
The name Cicada 3301 isn't arbitrary. The life cycle of the cicada insect which is based on prime numbers. Prime numbers are important in cryptography. And so, the image of the cicada insect became not only a logo but a recurring motif in the puzzles.
The core essence of Cicada 3301's puzzles gravitates around data security, cryptography, steganography, and internet anonymity. In other words, staying anonymous. This is important to remember.
These puzzles have earned Cicada 3301 a reputation as the harbinger of "the most elaborate and mysterious puzzle of the internet age". But why were they even created? Enter the conspiracy theories.
Cicada 3301 purportedly designed these puzzles to sift through the masses and recruit "highly intelligent individuals." While the ultimate goal of this initiative remains veiled in mystery, speculations are rife. Some theories posit that Cicada 3301 is a secret society. Others stretch the narrative towards a cult or religious sect. There's also chatter suggesting that the puzzles were a recruitment pipeline for the NSA, CIA, or MI6, or even cyber mercenary groups. Yet others speculate it's an alternate reality game, albeit one that hasn't been monetized by any individual or company.
Needless to say, there are a lot of theories but not a whole lot of answers. The purpose, identity, and the breadth of Cicada 3301's narrative continue to be a fertile ground for speculation and investigation, making it a captivating subject within and beyond the cybersecurity community.
The internet will tell you that the last Cicada puzzles was in 2014. However, users of the image board 4chan will tell you that the last posts appeared in 2017.
Q Posts
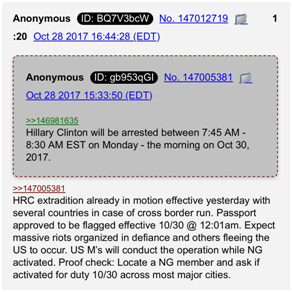
October 28, 2017, a series of posts on an image board called 4chan appeared. The conspiracy theory was initiated by an anonymous user known as "Q". "Q" began posting cryptic messages, with the first ones concerning an imminent arrest of Hillary Clinton.
Millions of people flocked to the boards to read these mysterious messages. Followers of Q became known as Anons. It was widely believed that Q compromised of a team of individuals (military insiders, powerful civilians, and President Trump whose posts were signed Q+) who were sharing information about a secret war being waged by then President Donald Trump against the "Deep State" - a cabal or network of influential people controlling the world. The name "Q" is thought to be derived from a US security clearance which typically stems from the Department of Energy.
From Day 1, both the media and the government attacked both the Q messages and the Anons who were "decoding the messages" (which basically means answering the questions that were being asked by the posts and tying them to current news stories). There were thousands of articles written to discredit the movement. Followers were labeled domestic terrorists by federal agencies. Cyber attacks were launched against 4chan, which later migrated to 8chan. This did not deter its popularity as more people became curious about the phenomenon.
But the movement didn't just attract followers. It also attracted a group of people thinking that they could capitalize off of a ready-made fan base.
Over time, the Q posts evolved to include a wide array of "conspiracy theories", some old and others new. Many of those conspiracies have been proven to be more fact than fantasy.
Ultimately, the movement, despite facing numerous platform disruptions and content bans on mainstream social media platforms, has demonstrated resilience, migrating to other platforms to continue propagating its ideologies. The movement has also found support and amplification from certain public figures and social media personalities, further fueling its growth and reach across different platforms and countries.
NOTE: There is no such thing as QAnon. There is Q and there are Anons.
Whoever Controls the Narrative, Controls the World
In an age where information is both a weapon and a shield, the narrative - the story told, the perspective shared, the version of truth propagated - holds immense power. Immense power. Whoever controls the narrative, in effect, shapes the perception of reality, steering the consciousness of the masses towards a particular direction.
This is not a new concept; it's a practice deeply rooted in the annals of history. You see it in every advertisement, every TV show, every news broadcast. Yet, in a digitally connected world, the reach and impact of narrative control has been amplified exponentially. Narrative shaping is a potent tool and a perilous weapon, depending on the hands that wield it.
The narrative forms the lens through which we view the world. It simplifies complex realities, provides context, and evokes emotions, making information relatable and understandable. This is the foundation of 5th Generation Warfare. Quiet weapons for silent wars. When a narrative is controlled by a particular entity or group, it shapes public discourse, molds opinion, and influences decision - YOUR decisions. Both on an individual and collective level.
This control over narrative is often pursued by various actors - governments, corporations, media houses, and groups of influential and powerful individuals. Each of these have their own set of interests and agendas.
In the political realm, narrative control is a linchpin for garnering support, neutralizing opposition, and directing the national discourse. By framing issues in a particular light - dictating the terminology, language, and definitions used and deciding which aspects are highlighted or omitted - those in control of the narrative can significantly impact public perception and, by extension, the political landscape. When you could control the political landscape, you control nations. When you control nations, you control the world, or globalization.
In terms of the movement, a well-crafted narrative can enhance reputability, evoke trust, and drive loyalty, while a tarnished narrative can lead to a loss of faith. So what does that mean to us?
The media, also called the fourth column, plays a crucial role in narrative formation and dissemination. However, in a scenario where media outlets are owned or influenced by political or corporate entities, the narrative can be skewed to serve vested interests, thereby compromising the integrity of information and misleading the public.
And when the public decides it has enough of the mainstream media, a market opens for independent journalists and reporters. Enter the social media influencers of our age and the drive to control them. The rise of social media has freed narrative control to some extent, allowing individuals and grassroots movements to challenge mainstream narratives and bring alternative perspectives to the fore. Except, it also paved the way for misinformation, echo chambers, and divisive narratives to flourish. But it went beyond this. Because it wasn't just the media influencers. It was this mysterious and powerful message being spread on the image boards 4chan and 8chan. Since it couldn't be discredited, it needed to be controlled.
Whoever controlled the narrative and the flow of information can control the world.
The B Drops
What better way to control the narrative than control the messages that were leading the people to freedom from those who were controlling that narrative? And there were many groups stepping up to the plate ready to do just that. If the boards couldn't be taken down, then why not fake the posts that were being posted there?
So a group called the Majestic 12 came together. Majestic 12 isn't the UFO and alien group that you are thinking about. The name was co-opted. Their mission was to take over the Q Research board on 4chan and later 8chan and ultimately the Q movement. They had a built in audience. All they had to do was obtain control.
So, the boards were hacked. Fake posts were made which looked like they came from the user posting as Q. The messages in these posts directed people to the Ingersoll Lockwood website. They used a VPN. It should have been untraceable. Except, it wasn't.
Every post has what is called an IP hash (a scrambled version of your IP which is attached to every post). The poster of the fake Q posts immediately posted under his Anon account in response to the fake Q posts. He was immediately caught. The community was understandably upset.
Jim Watkins, the owner of both 4chan and 8chan, was forced to launch an investigation. The posts were found to have been made by a Global Volunteer. Global Volunteer was an Anon who went by the name Baby Fist (aka Laughing Man, aka Ghosted). Once Baby Fist was identified, he made a post on GAB which said the following:
"Hello frens. This is one of the few platforms I have left. Wanted to let everyone know. I am not B. I am babyfist, Laughing Man, Patchf****, "George Orwell" or abcu8. Or any other name you wish to call me. I assume it was Sgt B who posted as B. We are frens and did work together to influence QR between 4/20 and 5/5 2020. I will not tell who Sgt B is so don't ask... We were clear and open of our intention then. I will always be clear and open with anons. I am not B. Sorry for any issues this has caused you @ JimWatkins and Q community."
It seemed like the matter was settled. Plot twist! A video emerges 6 months later showing Jim Watkins and an Anon who goes by the name Baby Fist in a Las Vegas hotel.
A QAnon revelation suggests the truth of Q’s identity was right there all along
Profile of a Syndicate
How do you infiltrate an online movement? For starters, it would involve a complex and highly orchestrated effort to infiltrate and potentially manipulate any movement. What resources would it take to do this?
Financial Backing
It would require significant financial resources. Why? Purchasing media companies, cybersecurity firms, and conspiracy theory sites would take a substantial and sustainable cash flow. This would be a critical element in executing any plan.
Organizational Structure
The organizational structure would be similar to a organized criminal enterprise. This would include hierarchies and chains of command. This organization would be structured in such a way as to emphasize on secrecy, loyalty, and control.
Political Motivation
Clear and specific political interests would be defined. This would include the purchase of media companies on BOTH sides of the political spectrum. Token personalities representing the opposite side of the aisle may be employed. Their goal may be to manipulate public opinion or protect their own interests.
Cyber Capabilities
This group would have the means to both hire individuals with hacking skills and potentially resort to blackmail, demonstrating a willingness to engage in illegal activities.
Information Warfare
The syndicate would engage in a form of information warfare. One method would be by targeting anonymous messaging boards where the movement's leader posts vital information. Coordinated disinformation campaigns would be launched through various conspiracy theory sites.
Secrecy and Anonymity
The syndicate maintains secrecy by using multiple layers of intermediaries, making it challenging to trace their involvement. It would also make it highly difficult to map their network.
A Strategy of Infiltration
Media Ownership
Through their acquisition of media companies on both sides of the political spectrum, the network would easily be able to control the narrative. Through this, they could manipulate public opinion by promoting or discrediting specific messages or individuals related to the movement.
Cybersecurity Companies
The acquisition of cybersecurity firms provides the organization with advanced tools and knowledge to infiltrate and disrupt the targeted messaging boards. They may exploit vulnerabilities, conduct DDoS attacks, or employ other hacking techniques.
Recruitment and Blackmail
This organization would recruit individuals with hacking skills or manipulates disgruntled insiders within the anonymous messaging boards. These individuals may be enticed with financial incentives or coerced through blackmail. Blackmail material may be obtained through the discovery of personal and private information, such as personal identities, information regarding family members, and information about current employment. Basically anything that could be used to extort control would be.
Disinformation Campaigns
The organization would spread disinformation through the conspiracy theory sites they control. Attempts would be made to create confusion, distract, and sow discord within the movement. By strategically releasing misleading or fabricated information, they can weaken the movement's cohesion and effectiveness.
Anonymity and Secrecy
They would take measures to hide their true identities and intentions. Some of these measures may seem extreme. Operating through intermediaries would be vital, using encrypted communication channels to avoid detection. Individuals would be set up to be ousted or targeted as a distraction should it be required.
Does any of this seem familiar?
A Personal Note
I currently fear for my personal safety. In the last week, I have had attacks that was more than just doxxing. But yes, I have been doxxed. Some of the information is correct. Some of it is wrong. I will not confirm or deny anything in order to keep my personal identity just that... personal.
I have never lied about who I am. I have always tried to be accurate in my message. The problem was I got a little too close to the truth.
If it was just a doxxing or trolling, I would have disregarded the attacks as normal. However, they weren't. Some of these attacks were beyond my technical understanding other than knowing it is possible.
Then there was the attacks against several other Anons. They were precise and purposeful. These attacks are coordinated. They aren't random. There is a very specific reason as to why they are happening.
I am going to expose that reason. And if something happens to me? There are others who have that information who can share it.
The only way to win the game is to change the rules. I changed the rules. We have it all.
To my attackers: I cannot be threatened. I cannot be coerced. I cannot be blackmailed. There is nothing you can do to me to stop what is coming. This is not a game.
To be continued...







After watching the last YouTube video I’m totally confused. Ron Watkins is Q.?? Sorry if I’m way off base. I’m more concerned for your personal safety than anything else. Thread is amazing.!! Can’t wait to read more. 👍👊💥
Whoever was behind the B posts looked to be trying to pull a fast one on the Q community.